Secure Grid Mode Configuration
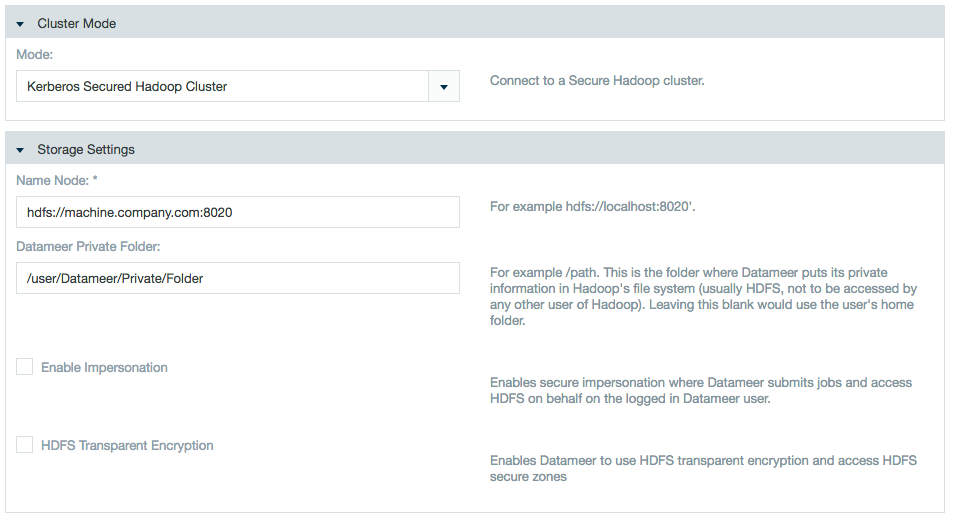
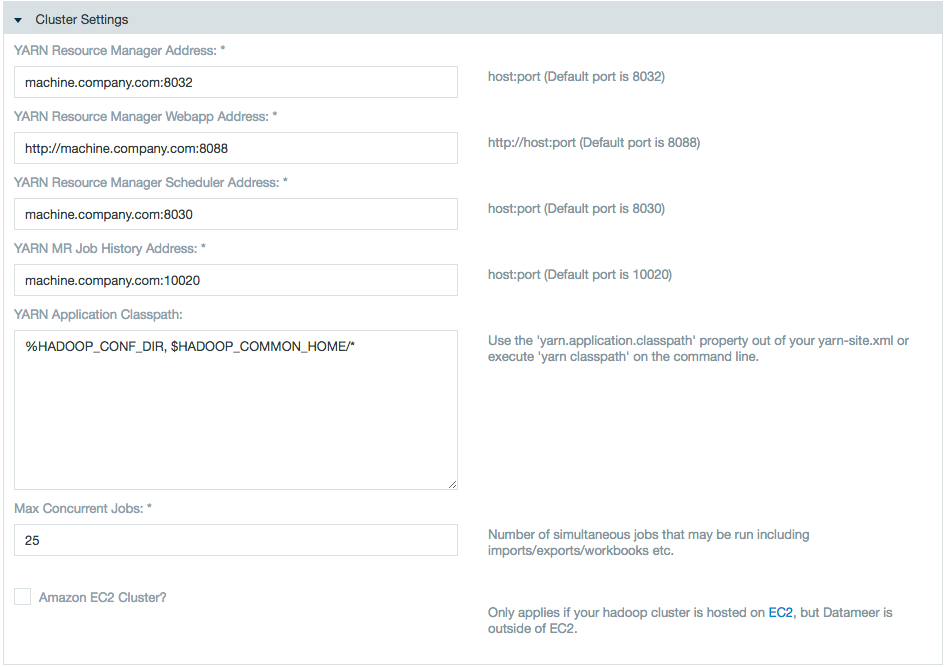
Secure Cluster Mode
Setting | Description |
|---|---|
HDFS Namenode | Full URI to the Namenode, e.g., |
Datameer Private Folder | Path to the Datameer user's directory on HDFS |
Job Tracker | Hostname and port of the JobTracker e.g., machine.company.com:8020 |
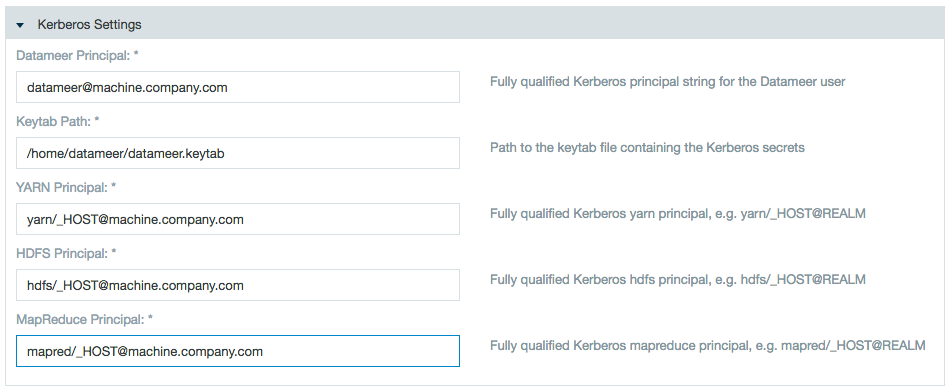
Datameer Principal | Fully qualified Kerberos principal for the Datameer user, e.g., |
Datameer Principal Keytab Path | Absolute path of the keytab file containing the credentials of the Datameer user, e.g., |
| Yarn Principal | Fully qualified Kerberos principal for the Namenode service user, user will almost always be
|
HDFS Principal | Fully qualified Kerberos principal for the Namenode service user, user is almost always be
|
Mapred Principal | Fully qualified Kerberos principal for the JobTracker service user, user is almost always be
|
Creating a Kerberos keytab
To create a keytab file for a Kerberos principal, das/machine.company.com@COMPANY.COM, run the ktuil application on a machine with Kerberos client software and access to the Kerberos realm.
ktutil: addent -password -p das/machine.company.com@COMPANY.COM -k 1 -e des3-cbc-sha1 <ENTER PASSWORD> ktutil: wkt das.keytab
This action creates a keytab file das.keytab which can now be used to authenticate the Kerberos principal.
Depending on your Kerberos realm's configured encryption types, the values for the -e argument might change. To find the avaliable encryption types look for the libdefaults section in your Kerberos configuration file, usually /etc/krb5.conf:
[libdefaults]
default_realm = LOCAL.NETWORK
dns_fallback = no
noaddresses = TRUE
default_tgs_enctypes = des3-cbc-sha1
default_tkt_enctypes = des3-cbc-sha1
permitted_enctypes = des3-cbc-sha1